What Do You Own and Where Is It?
It’s a simple question: What technology do we have and where is it? Unfortunately, the answer isn’t as easy.
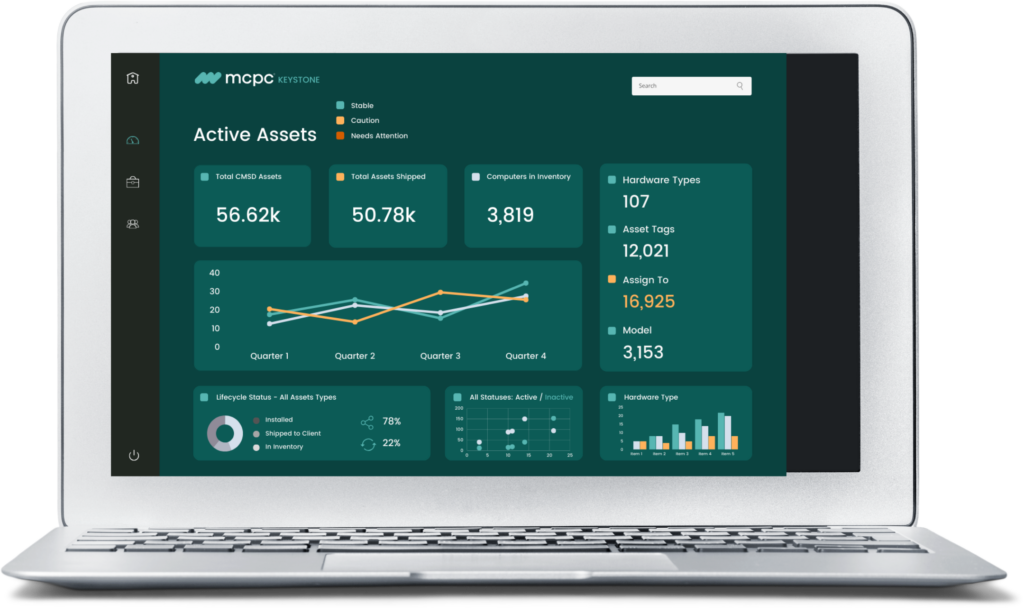
MCPC IT Asset Management brings simplicity to your endpoint management complexity by helping you answer that important question and provides comprehensive insight into all your hardware and software assets, because you can’t manage what you don’t know you have.
MCPC IT Asset Management provides:
- Visibility into your IT assets enterprise-wide
- Awareness of technology deployment, usage, costs, cycles, on-hand inventory, software compliance status, security patches and vulnerabilities
- Better and faster data-driven decision making